Organizations, particularly IT enterprises deploy web security applications to streamline their processes and grow their business. However, the vulnerabilities or cyber threats to these web applications can cause a headache.
The instances of cyber attacks have increased significantly in the recent past and did cost companies millions of dollars. According to cyber-observer, the estimated losses due to cyber-attacks are going to reach $6 trillion by 2021.
The same report also says that the spending on cybersecurity will likely reach $133.7 billion by 2022.
Usually, the major targets of cyber-attacks are web applications since they give easy access to a broad audience to spread malicious code faster.
In this post, we will talk about the 10 major web application vulnerabilities and the ways to stop them.
Major Security Issues of Web Applications
Most of the vulnerabilities occur due to authentication, validation, and user input flaws. These attacks are preventable by performing the basic actions correctly.
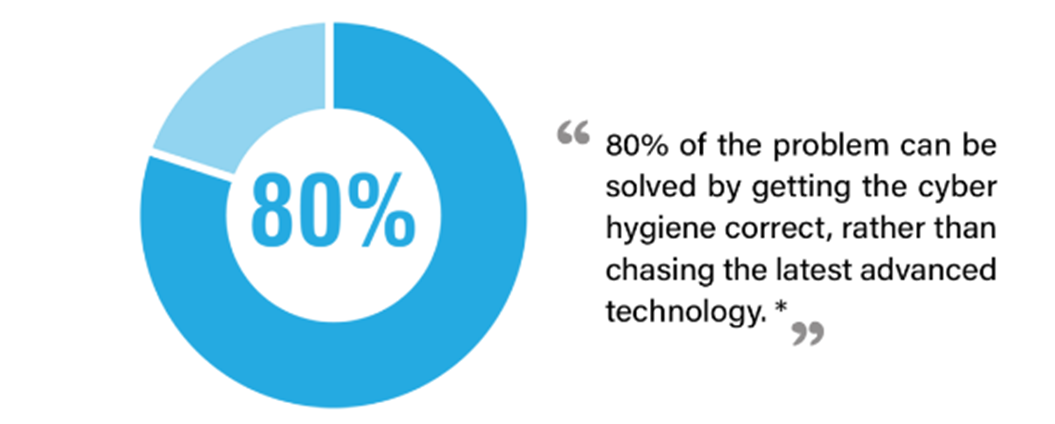
Source: cyber-observer.com
1- Injection Flaws
Injection flaws happen when unfiltered or unreliable data gets into a database or a server through a query. There are different types of injections, such as SQL, LDAP, NoSQL, OS, and more.
Out of these, most of the attacks take place by running SQL queries. SQL is mainly used to attack databases to get crucial data.
After getting unauthorized access, hackers can access users’ private information, including passwords, credit card details, and more.
How to Prevent It
You can prevent injection attacks by
- Validating the inputs. It will only allow data that is properly formed.
- Preparing statements with queries including certain parameters. It can effectively prevent SQL injections.
Not all parameters are specified when developing a statement. However, some time they are added at the time of execution. Hackers cannot modify these queries even with their own commands.
- Giving restricted user rights. To prevent injection attacks, only authorized users must get access to the database.
2- Breaching Confidential Data
Web application vulnerabilities also happen by accessing users’ confidential data, including account information, phone numbers, bank account details, credit card data, and more.
The user data breach may have serious consequences such as injection, broken authentication, or other issues.
How to Prevent It
- Robust data security: To prevent a data breach, it is important to encrypt data while storing and transmitting using the latest encryption techniques.
- Following security protocols: Make sure to implement advanced security protocols including SSL, TSL, and HTTPS for all types of inward data.
3- Bypassing Broken Authentication
By validating or authenticating user credentials, a system can identify true users.Credentials including passwords, biometrical data help to secure a web app. The term “broken authentication”refers to a breach of user credentials or session ID.
How to Prevent It
- Adding multiple authentications: Various ways of authentication like multi-factor authentication makes it easier to confirm the real users and prevent any breach.
- Allowing only strong passwords: Web applications should integrate specific conditions by setting strong passwords with a combination of complex and lengthy words, numbers, and symbols.
- Length of a session: Ideally a web application needs to trigger a message if a user session is idle for certain duration before closing it. This is a common practice in financial/banking sector.
- Security alerts: To secure user data, applying security alerts will notify users in case there are any suspicious activities in their accounts from a new device.
4- Broken Access Control
Another vulnerability issue for web applications is broken access control. This issue may crop up when attackers get access to the accounts of other users. They can modify information, check confidential information, and even take over the control of the application.
Issues relating to broken access control often crop up in a web application that did not run adequately while testing and lacks automated detection.
How to Prevent It
Enhanced access control: The design of access control systems is for role-based authentication. Also, there should be Access Control Lists (ACL) for approving or rejecting access to files/directories based on certain rules.
Denying access to backend functionalities: A web application should not give users access to backend functionalities, so that they cannot execute any action.
5- XML Entities (External) XXE
Security issues like using XXE attacks target web applications with XML input. These attacks usually happen because of XML processors that are outdated or badly configured.
Hackers can capitalize on this security hole to access the external systems/back-end and use it to execute SSRF (server-side request forgery) attack.
How to Prevent It
An effective method to keep off XXE attacks is deactivating the document type definition or DTD. If it is not possible to disable all the DTDs at once, you need to disable each of them separately.
6- Cross-Site Scripting (XSS) Attack
Vulnerabilities relating to XSS allow hackers to deliver dangerous JavaScriptto the browser of users. They do that by inserting a link.
If users click to check it, the hacker will sneak into the functionalities, including location and web camera. Attackers can even takeover the session and redirect users to malicious websites.
How to Prevent It
Input sanitization: It is about checking and cleansing data inputs from users. It will help to reduce the chances of exposing security vulnerabilities.
Data validation: Validating data will make sure that a web application is using correct information. In such cases, using whitelists can be handy.
7- Misconfiguration Attack
Misconfiguration of web applications often leads to security vulnerabilities and attackers capitalize on it.
Security misconfiguration includes unused pages, unpatched flaws, outdated software, unprotected files/directories, and using software in debug mode.
How to Prevent It
Consistent scanning for vulnerability: To prevent security misconfiguration, there is a need to scan the systems to identify any possible errors that hackers can use to get access.
Regular updates: Frequently updating web applications helps to minimize the chances of cyber attacks and protects user data.
8- Deserialization Attack
Insecure deserialization may lead to damages because of inserting unreliable data on web apps. It happens by executing malicious code remotely, bypassing validation, and modifying app logic.
How to Prevent It
Strict monitoring: The IT department of a company should strictly monitor and deny serialized objects that come from unidentified sources.
Restricted access: Executing the deserialization code after integrity checks like using digital signatures on serialized objects to prevent unauthorized access or data tampering.
9- Insecure Direct Object References
When the keys of a database or files are exposed to users, insecure direct object reference vulnerabilities might happen.
Due to unprotected internal objects, hackers can exploit them and get access to sensitive data. Sometimes authentication is either broken or non-existent.
How to Prevent It
You can prevent access to sensitive data through server-side input validation.
Testing server-side input can prevent hackers from manipulating file names and URL parameters.
Also, rolling out access control measures can help to find out if the user has permission to access or change files/databases.
10- Open Redirects & Forwards with Validation
Unvalidated or open redirects/forwards also cause vulnerability issue when hackers redirect a URL and forward users to an unreliable website using a parameter like GET requests.
After redirecting users, attackers try to steal crucial user data using malicious links or code.
How to Prevent It
You can prevent these attacks by preventing redirects. If needed, make redirects and forwards static which will not let users to input URLs.
Conclusion
Web application security is a major requirement of modern web development. To remain competitive and protect their reputation, companies have to figure out advanced security solutions to prevent malicious attacks and secure their customers’ data.
These 10 vulnerability issues and their preventions will give you a rough roadmap to beef up the security of your web apps and keep off cyber-attacks.
